KuCoin Releases Post-Quantum Cryptography (PQC) Gateway Proof-of-Concept
A forward-looking security practice, jointly exploring security solutions for Web2 and Web3 in the post-quantum era

In an era of rapid technological evolution, security is a continuous journey of exploration and progress. Quantum computing, as a cutting-edge technology, brings tremendous opportunities while posing a potential long-term threat to the current public key cryptography systems (such as RSA, ECC) that protect global digital security. Recognizing this trend, we choose to explore proactively rather than wait passively.
Today, we are pleased to share an important exploration result: KuCoin, in collaboration with the open-source project pqc-gateway (https://github.com/web3infra-foundation/pqc-gateway) under the Web3 Infrastructure Foundation (W3IF) and technical partner flomesh.io, has successfully completed the proof of concept (POC) for a quantum-resistant cryptography (PQC) gateway and opened it for public experience. This marks a solid step forward on our long journey towards post-quantum security.
About the Web3 Infrastructure Foundation (W3IF)
The W3IF Foundation (official website: https://web3infra.foundation/) is a non-profit open-source software foundation based in Hong Kong, aimed at gathering high-quality open-source Web3 infrastructure projects globally, promoting the construction of a decentralized technology ecosystem covering key areas such as consensus algorithms, zero-knowledge proofs, decentralized identity authentication (DID), and trusted computing. The pqc-gateway project, part of this collaboration, is an important component of the foundation's ecosystem.
- PQC, short for post-quantum cryptography or quantum-resistant cryptography. It does not refer to a specific algorithm, but rather a class of next-generation cryptographic algorithms that can withstand future quantum computer attacks.
- The core problem it addresses is: the security of widely used asymmetric encryption algorithms (such as RSA, ECC) is based on the computational complexity of certain mathematical problems. However, quantum computers can utilize their unique qubits (such as Shor's algorithm) to solve these problems in a very short time, threatening the security systems of everything from network communications to blockchain assets that rely on these algorithms.
- The value of PQC lies in the fact that even with powerful quantum computers, breaking PQC algorithms is theoretically very difficult. It aims to build a new security bridge that can traverse the "quantum era".
Global regulatory and standard-setting bodies have also taken active action, indicating the direction and urgency of this migration:
- The National Institute of Standards and Technology (NIST) has led and completed the standardization of the first batch of PQC algorithms (such as Kyber, Dilithium, etc.), marking a clear technological path [1]. At the same time, more algorithms have entered the final draft version, and the ecosystem is rapidly maturing.
- The National Security Agency (NSA) has issued a binding national strategy requiring the transition from traditional public key algorithms (RSA, ECC) to be completed around 2030. Starting from 2035, all new devices and software used for national security systems must only use PQC algorithms [2].
- The Securities and Exchange Commission (SEC) has also begun to prepare for the future, drafting a proposal for the global financial institutions titled "Post-Quantum Cryptography Readiness for the Financial Industry (PQFIF)", indicating that quantum-resistant security is about to become a hard requirement for financial compliance [3].
All of this indicates that the transition to PQC is no longer a question of "if", but rather "when" and "how".
In this context, KuCoin has partnered with the pqc-gateway open-source project and technical partner flomesh.io under the W3IF Foundation to put theoretical exploration into practice. Together, we have built a proof-of-concept environment for a quantum-resistant gateway.
Its core principle is: during the establishment of an HTTPS connection between the user's browser and the KuCoin server, the algorithms for key exchange and authentication are replaced from traditional RSA/ECC to the quantum-resistant (PQC) algorithms in the NIST standard draft.
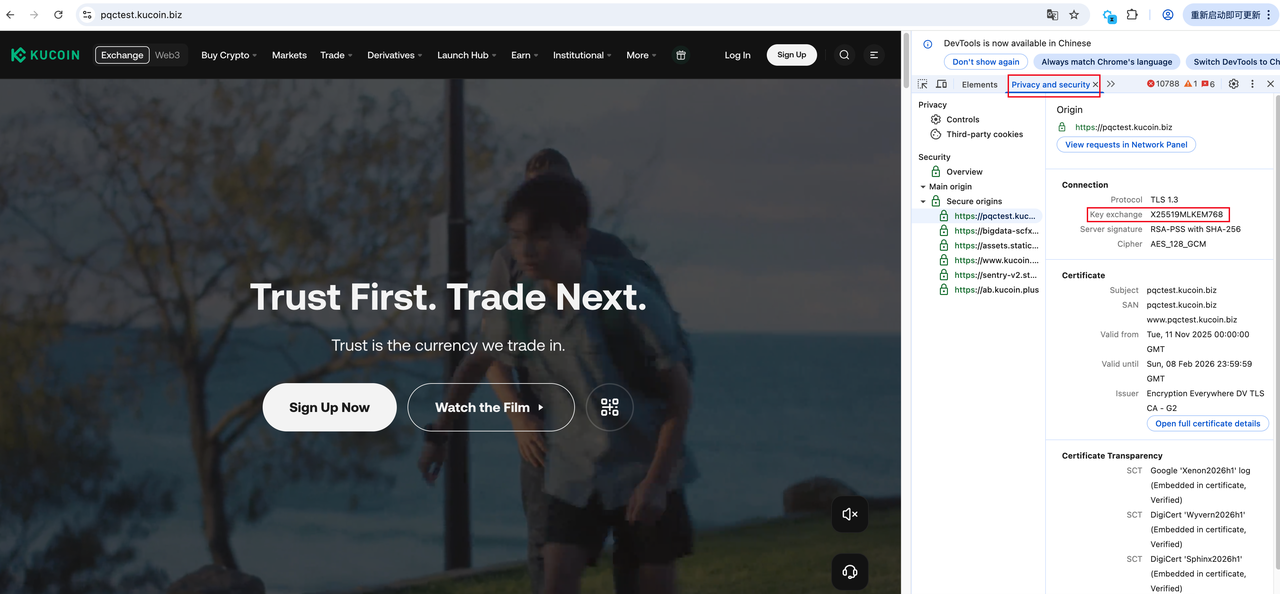
We sincerely invite you to experience this initial result: visit https://pqctest.kucoin.biz, your connection is already protected by post-quantum cryptography.
For the best experience, it is recommended to use the following browser versions:
- Chrome: Version 142.0.7444.135 and above
- Safari: Version 26.0.1 and above
- Firefox: Version 144.0.2 and above
For example, in the Chrome browser, press F12 to enter the console, select the Security panel, if your browser supports PQC, you will see under Connection in the Key exchange section that your key exchange algorithm has used the X25519MLKEM768 PQC algorithm, which indicates that your communication is protected by PQC.
Transforming PQC from theoretical standards to solutions usable in production environments is full of challenges. In this POC practice, we delved into several core issues with the W3IF Foundation's pqc-gateway project team and flomesh.io, which are also the "deep waters" faced by the industry as a whole:
1. Performance and Overhead: The art of balancing security and efficiency, as well as future optimization paths
This is the most direct challenge for the implementation of PQC, mainly reflected in the two aspects of computation and communication.
- Computational Overhead: The computational load of most PQC algorithms far exceeds that of current ECC. For example, the signature generation and verification speed of the signature algorithm Dilithium is several times to dozens of times slower than traditional ECDSA. For high-performance trading platform gateways like KuCoin, this means a significant increase in CPU load, which may directly affect the system's query rate and service latency.
- Communication Overhead (Bandwidth): This is currently one of the biggest pain points for PQC.
-
- Key Exchange: The ciphertext and public key size of the algorithm Kyber is about 1-2KB, while traditional ECDH is only 32-64 bytes.
- Signature: The signature size of Dilithium is about 2-4KB, while ECDSA signatures are usually only 64-128 bytes.
- Challenges of Certificates and Public Key Infrastructure (PKI):
- Certificate Chain Expansion: TLS certificate chains typically include end-entity certificates, intermediate CA certificates, and root CA certificates. If all use PQC signatures, the entire certificate chain size may reach several tens of KB. Browsers may need to download hundreds of KB of certificate data during the handshake, which can severely affect the first screen page loading speed and user experience.
- Overall Impact and Future Solutions: A complete TLS 1.3 handshake, if fully using PQC algorithms to replace existing algorithms, may cause the amount of data transmitted to surge by 10-20 times. This is a huge challenge for scenarios sensitive to network latency and bandwidth-constrained environments (such as mobile networks).
Looking to the future, we plan to work closely with the W3IF Foundation and its technical partners to explore systematic solutions together:
-
- Hardware Offload: Researching the use of dedicated hardware (such as smart network cards, cryptographic acceleration cards) to undertake high-intensity PQC computation tasks, freeing up the CPU to handle core business.
- Certificate Compression Technology: Exploring efficient compression algorithms to address the large size of PQC certificates, significantly reducing the amount of data transmitted without compromising security.
- CPU Instruction Set Optimization: Promoting and adopting CPU instruction sets optimized for mainstream PQC algorithms to enhance computational efficiency from the ground up.
Our goal is to ultimately achieve coexistence of security and efficiency through these technological innovations.
2. Protocols and Interoperability: The complexity of ecological collaboration
TLS is a complex protocol ecosystem, and introducing PQC requires collaboration from all parties, involving protocol extensions and certificate systems.
- Compatibility with the existing ecosystem and a gradual deployment path: Comprehensive and radical technological innovations are unrealistic at the level of internet infrastructure. Therefore, gradual deployment is the only feasible path.
- Resolved compatibility challenges: In this POC, we have successfully addressed compatibility issues with the existing ecosystem through clever gateway design and protocol negotiation strategies. Our gateway can intelligently identify the PQC support capabilities of the client (browser). For browsers that do not yet support PQC, the gateway can seamlessly fall back to traditional encryption algorithms, ensuring that all users can smoothly access the website, thus ensuring universal availability of the service. This is a key progress we have made in this practice.
- The current state and limitations of browser support: Why you currently only see PQC at the key exchange level.
Currently, mainstream browsers (Chrome, Safari, Firefox) are in the early stages of supporting PQC. Their support strategy is gradual and phased:
-
- Priority support for key exchange: Current browser versions primarily integrate support for PQC algorithms (such as Kyber) at the key exchange stage. This is because key exchange directly affects the security of session keys for subsequent communications, which is key to protecting against 'store now, decrypt later" attacks. Therefore, when you access our test domain, your browser is already able to negotiate a quantum-resistant session key with our gateway using PQC algorithms.
- Lag in digital signature support: In contrast, support for digital signatures (mainly used for server identity authentication, i.e., certificate chain verification) is still being improved in browsers. This is why, in the current experience, the application of PQC is mainly reflected at the key exchange level. The entire industry still needs to wait for browsers and certificate authorities (CAs) to fully follow up on the signature level.
3. Security management of sensitive key materials
Cryptographic upgrades are not just about changing algorithms; they also impose new requirements on the management of the entire security lifecycle. How to securely generate, store, rotate, and destroy the private keys corresponding to the PQC algorithm, ensuring that these new, potentially more complex sensitive information is not leaked, is a challenge that is more complex and critical than the algorithm replacement itself. We are adapting and validating the existing mature key management system with the new features of PQC.
Despite many challenges, the POC validation of this gateway has opened the door to broader PQC application scenarios for us. The security of the trading platform is just the starting point; the security of the blockchain itself, especially the security of wallets and smart contracts, also faces challenges from quantum computing. In the future, we will extend our exploratory vision to the on-chain field, committed to safeguarding users" comprehensive digital asset security:
- Quantum-resistant wallets: Exploring the use of PQC algorithms to generate and store private keys, or constructing quantum-resistant signature schemes to fundamentally protect wallet assets from future quantum computing threats.
- Secure DApp applications: Supporting and promoting DApp developers to use PQC algorithms for user identity authentication and transaction signing, building a post-quantum security foundation for the entire decentralized application ecosystem.
- On-chain transactions and smart contracts: Researching new generation transaction signature formats and smart contract verification mechanisms compatible with PQC, ensuring that on-chain operations remain secure and trustworthy in the quantum era.
Our vision is to build a three-dimensional quantum-resistant security protection system from trading platforms to blockchain networks, from centralized services to decentralized applications, truly safeguarding everyone's on-chain security.
This collaboration POC with the W3IF Foundation, flomesh.io and its pqc-gateway open-source project, along with our in-depth analysis of challenges and future planning, is just a starting point for KuCoin on the long road of post-quantum migration. We do not dare to claim that we have solved all problems, but we firmly believe that early exploration, active practice, and open cooperation are the best ways to cope with future uncertainties.
KuCoin always regards the security of user assets and data as its primary responsibility. Through comprehensive exploration from trading platforms to the blockchain ecosystem, we aim not only to enhance our own security technology barriers but also to accumulate best practices for the industry in implementing PQC. We look forward to working with more partners and users to jointly build a more secure digital asset ecosystem that can confidently face the next computing era.
Because true security comes from a reverence for the future and actions that begin at our feet.
References:
[1] NIST PQC Standardization: https://csrc.nist.gov/projects/post-quantum-cryptography/selected-algorithms-2022
[2] NSA Cybersecurity Advisory - PQC Migration: https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3498776/post-quantum-cryptography-cisa-nist-and-nsa-recommend-how-to-prepare-now/
[3] SEC - PQFIF Draft Recommendations: https://www.sec.gov/files/cft-written-input-daniel-bruno-corvelo-costa-090325.pdf