Web3 Wallet Security Guide: Building Your On-Chain Vault
I. Understanding the Core Risks of Web3 Transactions
Why is extreme caution necessary in blockchain transactions?
Types of Signatures: Transactions vs. Messages
-
Transaction Signatures: Authorize actions to take effect on-chain, such as transfers, token swaps, or interactions with smart contracts.
-
Message Signatures: Generally do not directly transfer funds, but certain formats (e.g., Permit, eth_sign) can be exploited as hidden authorizations to access your assets.
II. Pre-Signature Checklist
✅ Recipient Address
-
Don’t rely on just the first or last few characters—compare the full address character by character.
-
Never copy directly from transaction history to avoid falling victim to “poisoned address” scams.
✅ Transaction Details
-
Confirm both the token (e.g., USDT, USDC) and the blockchain network (e.g., Ethereum) align with your intended action.
✅ Signature Request Content
-
Are there unreadable characters or random strings?
-
Does it reasonably match the action you’re performing in the DApp?
-
If unsure about the purpose of the signature, stop immediately and research before proceeding.
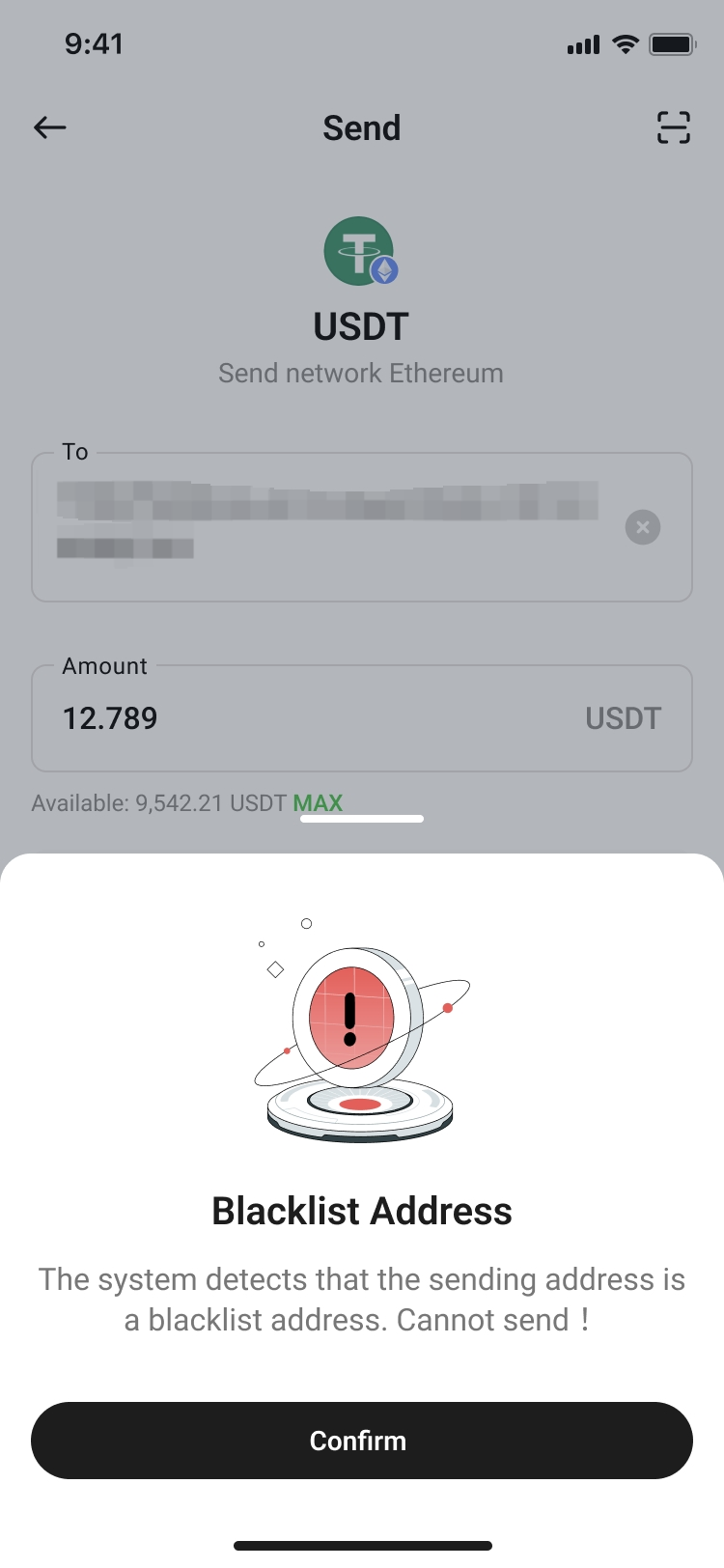
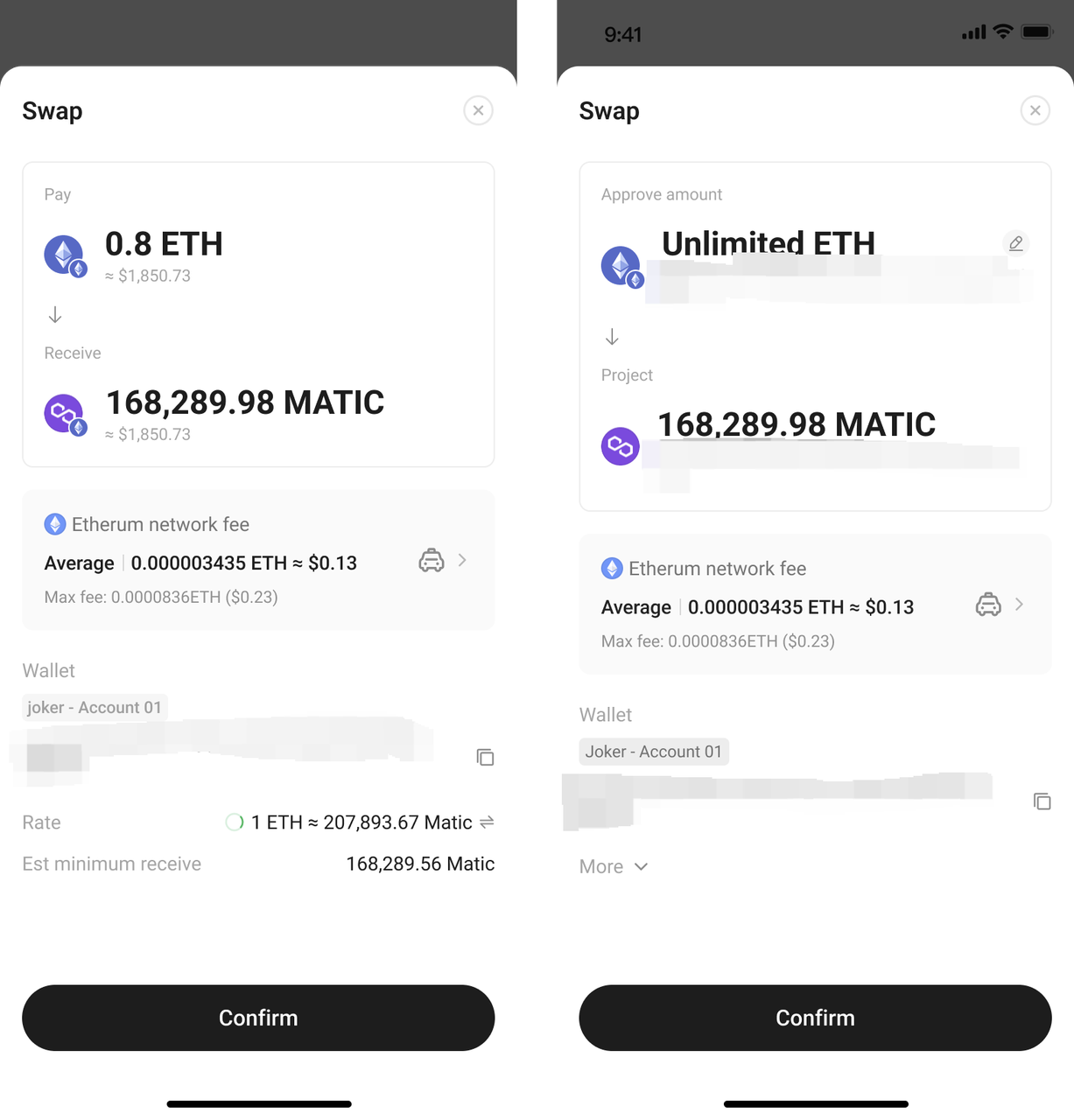
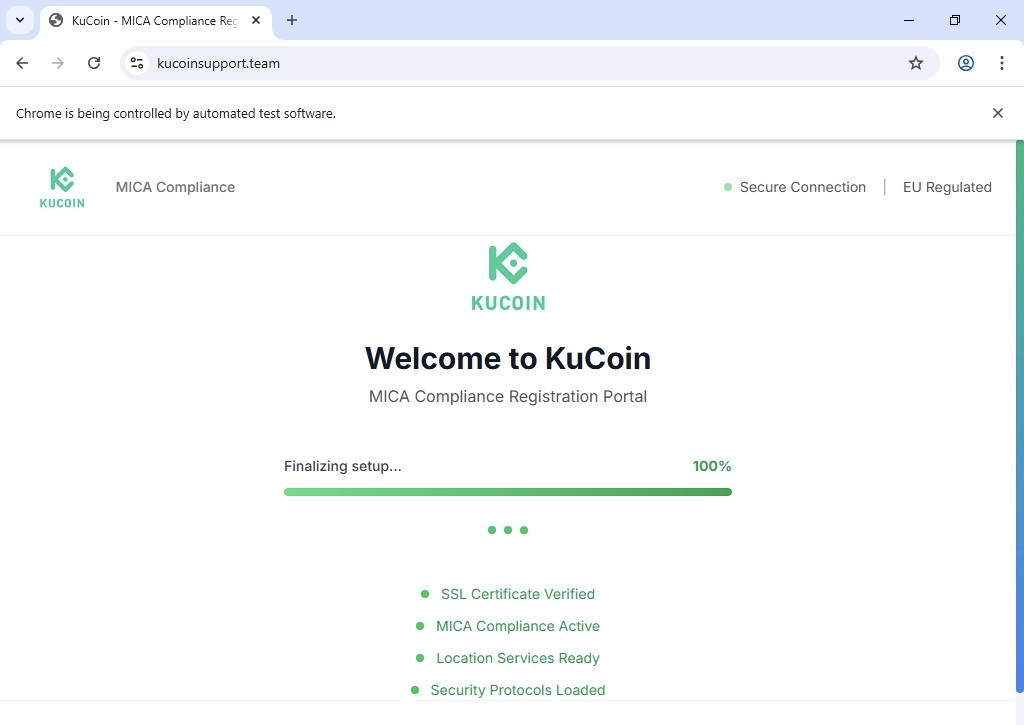
III. Beware of Common Web3 Scams
| Type | Scam Tactics | Protection Tips |
| Poisoned Address Trap |
Scammers forge "fake addresses" similar to your commonly used ones, sending worthless tokens to you in an attempt to trick you into copying this address during the next transfer. |
1. Always copy addresses from trusted sources. addresses. address before executing larger transfers. |
| Phishing Website |
Fraudulent websites that impersonate official ones, enticing users to connect wallets and authorize signatures to steal assets. |
1. Avoid clicking on links sent by strangers. official bookmarks to visit. prompts, always verify through official channels. |
| Fake Airdrop/NFT Bait |
Unknown tokens or NFTs appearing in your wallet, possibly containing malicious code or bait links that trigger dangerous authorizations when clicked. |
1. Never interact with assets from unknown sources. transfer, or approve them. |
IV. The 5 Golden Rules of Web3 Wallet Security
-
Research DApp Background: Before connecting your wallet, investigate the project team, community, and whether its smart contracts have been audited.
-
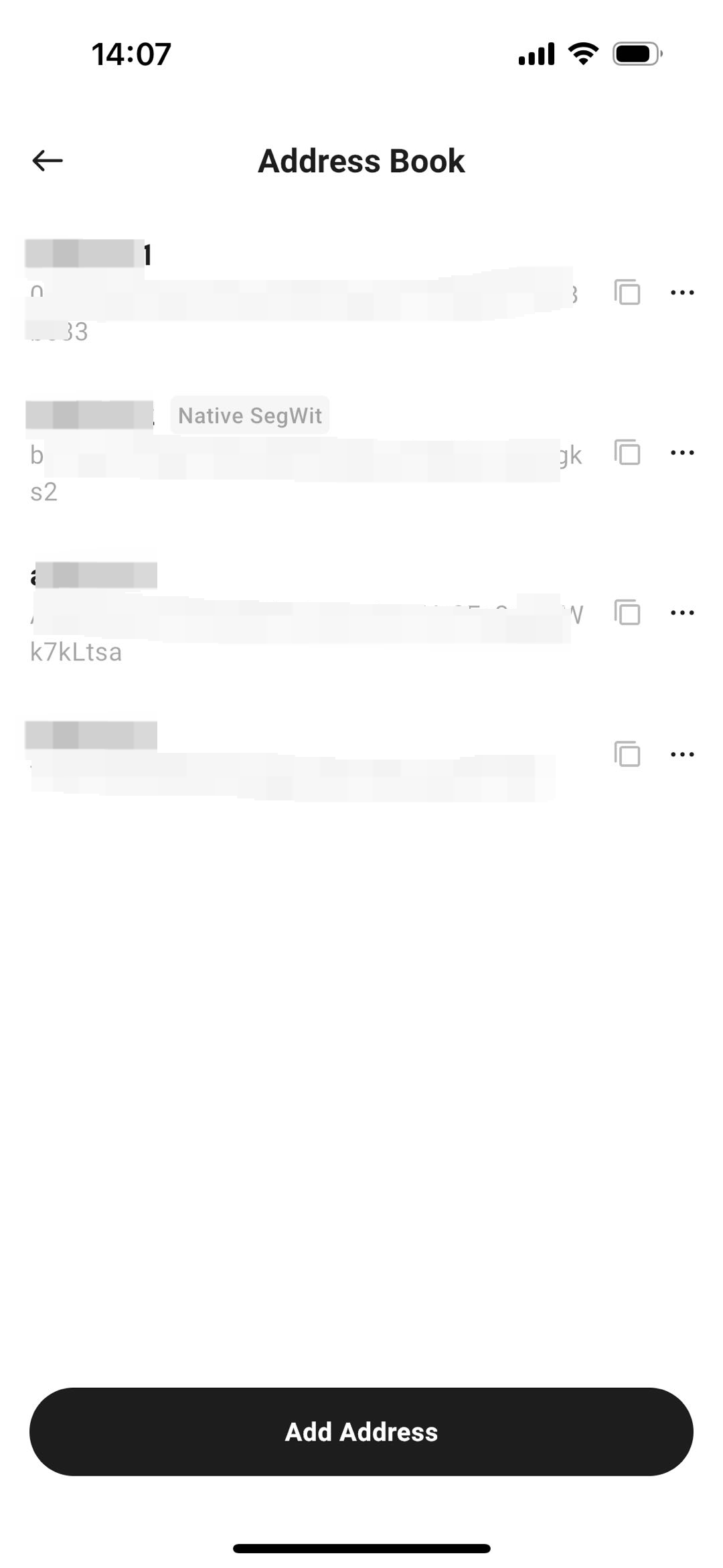
Avoid Copy-Paste Operations: Clipboard data can be tampered with—use your address book instead.
-
Save Trusted Addresses: Manage frequently used addresses securely within your wallet’s address book feature.
-
Verify Addresses Character by Character: Don’t rely on just the first or last digits; scammers exploit this habit.
-
Heed Warnings and Prompts: Treat all wallet risk alerts as serious red flags.